Blog
April 20, 2021
It’s an ingrained habit to lock the doors to our houses and our cars, as well as provide virtual locks on our online accounts using passwords. Why not take the same precautions for the data in our API tests? In BlazeMeter, we take security measures very seriously and offer you an additional way to “secure” your valuable information via our Secrets Management feature for your API monitoring tests.
In 2018, we released Secrets Management at the team level in what was formerly our Runscope API Monitoring solution. As you may know, the Runscope capabilities you know and love are now an integral part of the API Testing & Monitoring functionalities in the BlazeMeter Continuous Testing Platform. Our team is excited to share that we have expanded upon our Secrets Management feature to now support secrets at the bucket level.
Keep reading to learn more about this feature, including how it works at the team and bucket levels.
What is Secrets Management?
Back to topWith secrets management, teams can successfully manage digital authentication credentials (secrets) such as passwords, APIs, keys, and tokens for use in applications and other sensitive parts of the IT ecosystem. It covers all processes and tools related to digital credentials.
What is Secrets Management in API Monitoring?
The Secrets feature allows you to keep sensitive information secure, now available at both the team and bucket level. You might have a .env or config file in your application that includes sensitive variables that you don't want to be checked into your project's version control repository. Our Secrets feature allows you to “mask” your data, and lets you keep sensitive information that you specify secure.
Please note: The Secrets Management feature requires a qualifying plan. Check your plan or contact Sales to get started.
Back to topWhen Should You Use Secrets Management?
Secrets Management is important to ensure that sensitive information like encryption keys, passwords, credentials, API tokens, SSH keys, and more - are not breached. Here are some common use-cases where you might benefit from this feature:
- You might have an API key or access token that you do not wish to be visible in your tests for security reasons.
- You're working with an API that requires authentication credentials that you don't want exposed.
- You don't want to send certain information to third-party integrations.
How Does Secrets Management For DevOps Work?
Team owners and administrators can create and manage variables with a key and value pair. Although the value is encrypted and hidden, team members can reference the variable by referencing the respective key in the tests that they create.
Let’s take a look at the following example, where we have designated a value that we want to keep hidden, and the key that will unlock or reference the hidden value:
Value = top-secret-data
Key = opensesame
Instead of a tester referencing top-secret-data in their test, they can instead reference this value in their tests via the designated key with this built-in function: {{get_secret(opensesame)}}.
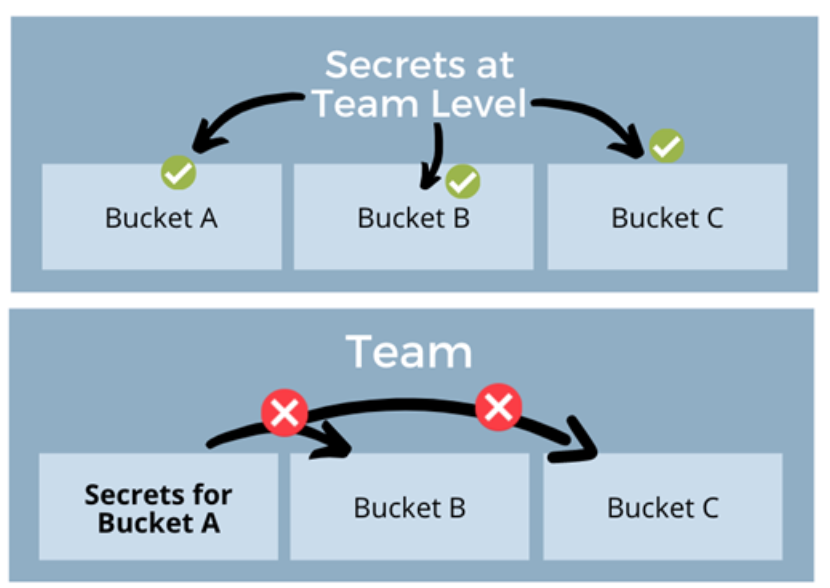
Back to topSecrets Management at the Team vs. Bucket Level
As a team owner or admin, you can create and manage secrets at the team level and at the bucket level. Here are some important points to note about using secrets at these levels:
- Secrets created at the team level can be used by all tests in all buckets of that team.
- On the other hand, Secrets created at the bucket level can be used only by tests contained within that bucket, and cannot be used by other buckets, even if they reside within the same team.
Get Started With Secrets Management
To learn more about using Secrets Management including how to manage, edits and delete secrets, view the step-by-step guide in our documentation: Secrets Management.
If you haven’t already, you will need to designate the correct role-based access controls to manage the necessary users’ access to managing, editing, and viewing specific tests, buckets, and account features.
Related Resources: